Updated April 2024: Stop getting error messages and slow down your system with our optimization tool. Get it now at this link
- Download and install the repair tool here.
- Let it scan your computer.
- The tool will then repair your computer.
COM Surrogates are processes that run a COM object outside its main process. They can cause problems because they consume resources such as memory or disk space. You can use the Registry Editor to disable them temporarily. This windowsbulletin article explains how to fix COM Surrogate high CPU or disk usage in windows 10.
What is a COM Surrogate?
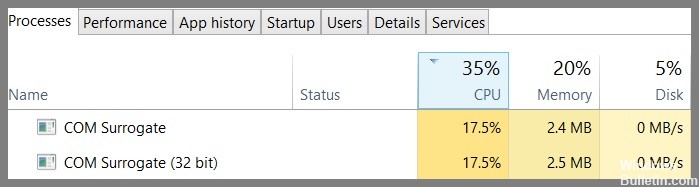
COM surrogates are an integral part of the Windows operating system. These are small programs that help Windows run smoothly. You can think of it as a translator – it translates the code written in one language into another. For example, let’s say you want to use a particular program called “MyApp”. If MyApp doesn’t support Windows 10, you won’t be able to download it. In such cases, a COM surrogate helps the app work on Windows 10.
COM surrogates are used to host DLL files. A DLL file contains executable instructions that perform specific tasks. Without a DLL file, Windows wouldn’t know how to execute those instructions. So, whenever you install a new application, you might see a file named “dllhost.exe”. That’s because the installer needs a COM surrogate to load the DLL file.
Is COM Surrogate a Virus?

COM surrogates are not viruses; however, they can cause damage to a computer if they are designed in such a way that it looks like a virus. They can come in different forms, including modifying registry settings or creating an executable file.
There are many ways to create COM surrogates, including modifying registry settings and creating an executable file. These methods include modifying the registry settings, adding a.reg file, or renaming the original file and placing it into a folder where it is executed automatically.
When a COM surrogate is detected by the operating system, Windows displays a warning message and asks whether you want to remove it. If you choose to delete the file, you will lose access to some functions of the program. However, there is no harm done to your computer unless you allow the program to run without being checked.
Why does the problem occur?

Ransomware is one of the biggest threats to our personal data today. It has been around since the early 2000s, but it has become much more prevalent over the past few years. In fact, there are now thousands of variants of ransomware out there, each targeting a specific type of device or operating system. While we don’t know exactly how many people are affected by ransomware, experts estimate that it costs businesses $1 billion every month due to lost productivity and downtime.
The good news is that there are several things you can do to protect yourself against ransomware. Here are some of the most important ones.
Keep your operating system up to date: One of the best ways to prevent a ransomware attack is to keep your operating system up to date. This includes keeping your antivirus software updated, installing patches for known vulnerabilities, and making sure your apps are running the latest version of the software. If you’re worried about privacy, make sure your browsers are set to use HTTPS connections whenever possible.
Back up your data regularly: If you’ve ever had your computer crash, you know how devastating losing everything can be. Unfortunately, ransomware doesn’t discriminate; it’ll encrypt just about anything on your hard disk. So, even though it might seem like a hassle to backup your files regularly, doing so could save you a lot of trouble later. You can use cloud storage solutions like Dropbox, OneDrive, Box, Gdrive, etc., to easily store copies of your documents online. Or, you can simply copy files to external drives or USB sticks. Either way, backing up your data regularly helps ensure that you won’t lose everything if something goes wrong.
Use strong passwords: A strong password is one of the easiest ways to avoid getting locked out of your own computer. The longer the password, the better, as long passwords tend to be harder to crack than short ones. But, don’t go overboard with your password strength. A good rule of thumb is to have at least eight characters (including numbers, letters, and special symbols) and mix upper-case and lower-case letters in different combinations. Also, try not to repeat any words or phrases within your password.
Don’t click on links from untrusted sources: While this may sound obvious, clicking on links from untrusted sources can lead to malware infections. That’s why it’s always a good idea to check the URL before opening a link. For example, if you see an email address ending in @hotmail.com, chances are it came from someone who wants to scam you. Instead, look for addresses ending in.org,.net, or.edu. These are all legitimate websites.
Install antivirus software: Antivirus software is another great way to help protect your PC from ransomware attacks. There are two main types: signature-based and heuristic-based. Signature-based programs scan your entire drive looking for malicious code. They then compare what they find to a database of known viruses. Heuristic-based programs work differently. Rather than scanning your entire drive, these programs only scan files when they open them. As soon as they detect a virus, they delete it automatically. Both types of antivirus software are effective against most ransomware threats. However, some ransomware variants can bypass both types of protection. In those cases, you should consider using a third-party program.
Launch the SFC scanning
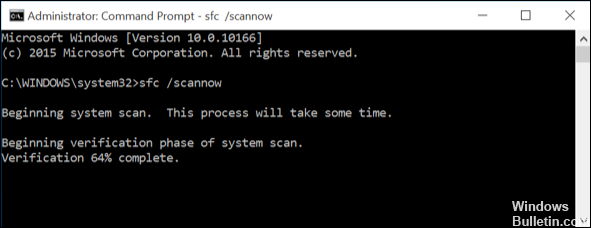
The System File Checker scans your computer for missing or corrupt system files. It also checks whether there are problems with the registry.
- Type sfc /scannow into the search box. Click OK.
- If the Scanning progress bar appears, wait until it finishes. When it does, click Finish.
- Restart your computer after executing the scanning process.
The scanlog.txt file contains information about what files are infected and where they are located on your hard disk. This log file can be used to determine whether you want to delete the virus.
April 2024 Update:
You can now prevent PC problems by using this tool, such as protecting you against file loss and malware. Additionally it is a great way to optimize your computer for maximum performance. The program fixes common errors that might occur on Windows systems with ease - no need for hours of troubleshooting when you have the perfect solution at your fingertips:
- Step 1 : Download PC Repair & Optimizer Tool (Windows 10, 8, 7, XP, Vista – Microsoft Gold Certified).
- Step 2 : Click “Start Scan” to find Windows registry issues that could be causing PC problems.
- Step 3 : Click “Repair All” to fix all issues.
Start DISM tool
DISM is a built-in tool in Windows 10 that helps users troubleshoot and resolve issues related to.wim files. DISM scans the.wim file and reports errors or missing components. DISM allows you to fix corrupted registry keys, which can lead to unexpected behaviors in Windows.
To use DISM, follow these steps:
- Click Start, type dism in the Search box, and press Enter.
- Select Create a new image, and then click Next.
- On the Select source media screen, select the.wim file you created earlier.
- On the Specify a name and location for the image screen, enter a descriptive name for the image.
- Click Save.
- When the image has been saved, click Close.
Uninstall the recently installed driver
Sometimes, installing a new driver won’t work correctly. If you’re having trouble getting it to install, try uninstalling it first. This will clear out any leftover files and allow you to reinstall it without problems.
- Open Device Manager by pressing Ctrl+Shift+Esc.
- Right-click each device listed under Display adapters, Network adapters, Sound cards, USB controllers, and other devices, and then choose Uninstall.
- Repeat the process for each item listed above.
- Reboot your computer.
Update the antivirus software
Antivirus programs are essential tools for protecting computers against malware and viruses. But many people still use free antivirus software, which often doesn’t provide the same level of protection as paid products. Many free antivirus programs come bundled with adware, spyware, and potentially unwanted applications (PUAs).
This can lead to problems with Windows components like COM Surrogate. If you experience issues related to COM Surrogate, it could mean that your computer has been infected with malicious software. You can check out our guide on how to fix COM Surrogate errors.
Close COM Surrogate using the Task Manager
Users are receiving error messages when attempting to modify image metadata. This could be due to a number of issues, including incorrect file permissions, registry settings, or even missing files. In some cases, it could be caused by a corrupt DLLHost.exe process. If you receive this error message while editing images, try closing the COM Surrogate process.
- Rightclick dllhost.exefind “COM Surrogate”and select End Process.
- You can also use Ctrl+Shift+Esc to open the task manager.
- Find the process and end it.
Perform a clean boot
A clean boot state will help you identify any hardware issues. If you are experiencing slow performance or freezing during startup, it could be caused by malware or another program installed on your computer.
To perform a clean boot, follow these steps:
- Restart your device.
- Press and hold Shift while restarting your device.
- Select Troubleshooting options.
- Choose Startup Settings.
- Click Advanced Options.
- Select Safe Mode.
- When prompted, confirm that you want to start in safe mode.
- Wait until the system reboots into Safe Mode.
- Perform a complete scan of your PC from the Microsoft Security Essentials (MSE) app.
- Reboot normally after the scan completes.
Scan with Antivirus Software
Popup ads aren’t always what they seem. They’re often used by hackers to trick you into downloading malware onto your PC. If you see a popup ad that looks suspicious, don’t hit “OK.” Instead, scan your computer with antivirus software to make sure there isn’t anything nasty lurking inside.
If you use Windows 10, Microsoft offers built-in tools to scan your machine for problems. This tool will look for known exploits and vulnerabilities in your operating system and tell you how many threats it found.
Expert Tip: This repair tool scans the repositories and replaces corrupt or missing files if none of these methods have worked. It works well in most cases where the problem is due to system corruption. This tool will also optimize your system to maximize performance. It can be downloaded by Clicking Here
Frequently Asked Questions
What is a COM Surrogate process?
The Component Object Model (COM), or simply COM, is a standard way for applications written in different programming languages to interact. This method is used to build software components that work together. For example, you might use it to make sure that a photo editing program doesn't crash while saving images. You could also use it to connect to databases and retrieve information.
COM works well because it creates a sort of bridge between two separate programs. However, it does come with some drawbacks. One of those problems occurs when one component fails, causing the entire system to stop working. In the case of Windows, it happens when a single COM object fails. When that happens, the whole operating system stops functioning properly.
Should I disable COM Surrogate?
COM Surrogate is a feature of Windows 10 that allows applications to access shared memory across processes. Applications use it to communicate with each other, but you don’t want to turn it off because it’s essential to running some programs.
How to get rid of the COM Surrogate virus?
The COM Surrogate virus doesn't do anything harmful itself, but it does spread throughout your computer system. Once installed, it starts looking for other viruses like Trojans, worms, spyware, etc. that might be lurking around. When it finds those things, it downloads them too.
If you're infected with the COM Surrogate, there are three easy steps you can take to clean up the mess.
- Run a computer scan.
- Use a third-party antivirus.
- Reboot your computer.


